
IT Service Desk
WATCH THE VIDEO ➔ |
Empower Your Team with an IT Service Desk That Lets Them Focus on Work
95% SLA Compliance
At Core, we consistently meet agreed service levels to ensure reliable, high-quality support.
rate (FCR) – frequently surpassing 90% during peak performance periods.
24/7 Availability & Instant IT Service Desk Support
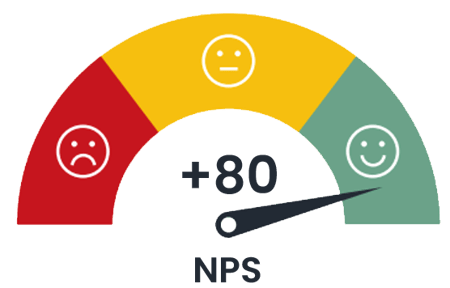
World-class user satisfaction
We put customer satisfaction at the heart of everything we do, and it shows—our IT service desk has achieved a Net Promoter Score of +80, far surpassing the ‘World-Class’ benchmark of 70 and reflecting our strong commitment to delivering an exceptional user experience.
Why should you choose Core as your IT Service Desk?
Because you’ll get a team that feels like an extension of your own—always on hand, quick to respond, and built around the way you work.
Fully outsourced Service Desk function.
Incident logging and triage to 2nd and 3rd line teams.
Our focus on first-time fix will keep your employees productive.
Third-party escalation and management.
Dedicated team for your business.
Follows ITIL v3 and v4 frameworks.
Our shift-left approach
The shift-left strategy is at the heart of our service, enhancing business knowledge and contributing to consistently high FCR rates of 75% or more.
By incorporating this approach as a standard feature, we challenge the conventional workflow and propel resolution and fulfilment duties directly to the IT service desk.
This strategic move adds immense value by enabling our engineers to resolve incidents on the spot, significantly reducing the need for escalation.
Core IT Service Desk
Our Managed Service Desk has been developed with the end user in mind, focusing on first-time fix, effective communication, and continual improvement.

Ready to elevate your IT support experience
Don’t let IT challenges slow your business down. Contact us to learn more about how Core can transform your IT operations, enhance user satisfaction, and contribute to your success story.
Speak with one of our IT service desk experts to tailor a support solution that aligns with your unique needs.
FAQs
An IT Service Desk is the first point of contact for employees when something goes wrong with their technology. From resolving everyday issues like password resets or connectivity problems, to escalating more complex technical challenges, the service desk keeps people working efficiently and ensures your business technology runs smoothly.
A service desk helps your company by providing a central point of contact for all technology issues, ensuring problems are resolved quickly and effectively. It reduces the burden on your in-house IT team, cuts costs through automation of routine tasks, and enhances business processes by streamlining communication between users and IT.
Because we understand that every organisation is different. Whether you need round-the-clock coverage or extra support to ease the pressure on your in-house team, we’re flexible, responsive, and experienced—giving your people the help they need, exactly when they need it.
What our customers say about us


Core have been outstanding to work with. They really listened to what we were trying to do, talked through all of their ideas, and fully explained the pros and cons involved while taking into account our long-term business goals.

Over the years, Core and the University of Law have built a strong relationship based on trust, expertise and knowledge. Core has always listened to and addressed our specific needs, before tailoring a specific and precise solution, whether that be delivering a successful SharePoint Online project, or when approached for some guidance or advice around Dynamics 365 licensing. We very much look forward to collaborating on future projects with Core.

It was apparent from day one that Core had a depth of knowledge in Microsoft 365, which we simply hadn’t found anywhere else.
With pre-purposed training modules and the ability to tailor training to our specific needs, Core ticks all the boxes. What may have taken weeks to prepare by way of training materials, instead took only days.

Core have helped us with various projects, from initiation to delivery for web development to app deployments, and they have always shown a high level of expertise and creativity. Core is not just a solution provider, they are also a trusted advisor who take time to understand our needs and goals to ensure our investment delivers value to the business. In an age where supplier engagement can be painful, it has been a pleasure working with Core since the outset!

Check out our latest blog posts
Keep up to date with the latest insights from Core's team of subject matter experts through our engaging and informative blog topics.
Is Copilot Good? The Benefits No One Tells You About
How to Create a Copilot Agent
Microsoft Copilot vs ChatGPT: What You Need to Know
Let's talk
For more information about Core or to discuss your project, contact our friendly experts today.






